A few weeks ago, we talked about PwnFox and the Burp Suite extensions Autorize to test IDOR vulnerabilities. In the follow-up of this article, today we’d like to introduce you to the Auth Analyzer plugin. This plugin enables the creation of multiple sessions simultaneously to help you test horizontal and vertical privilege escalation.
Description from the author: The Burp extension helps you to find authorization bugs. Just navigate through the web application with a high privileged user and let the Auth Analyzer repeat your requests for any defined non-privileged user. With the possibility to define Parameters the Auth Analyzer is able to extract and replace parameter values automatically. With this for instance, CSRF tokens or even whole session characteristics can be auto extracted from responses and replaced in further requests. Each response will be analyzed and tagged on its bypass status.
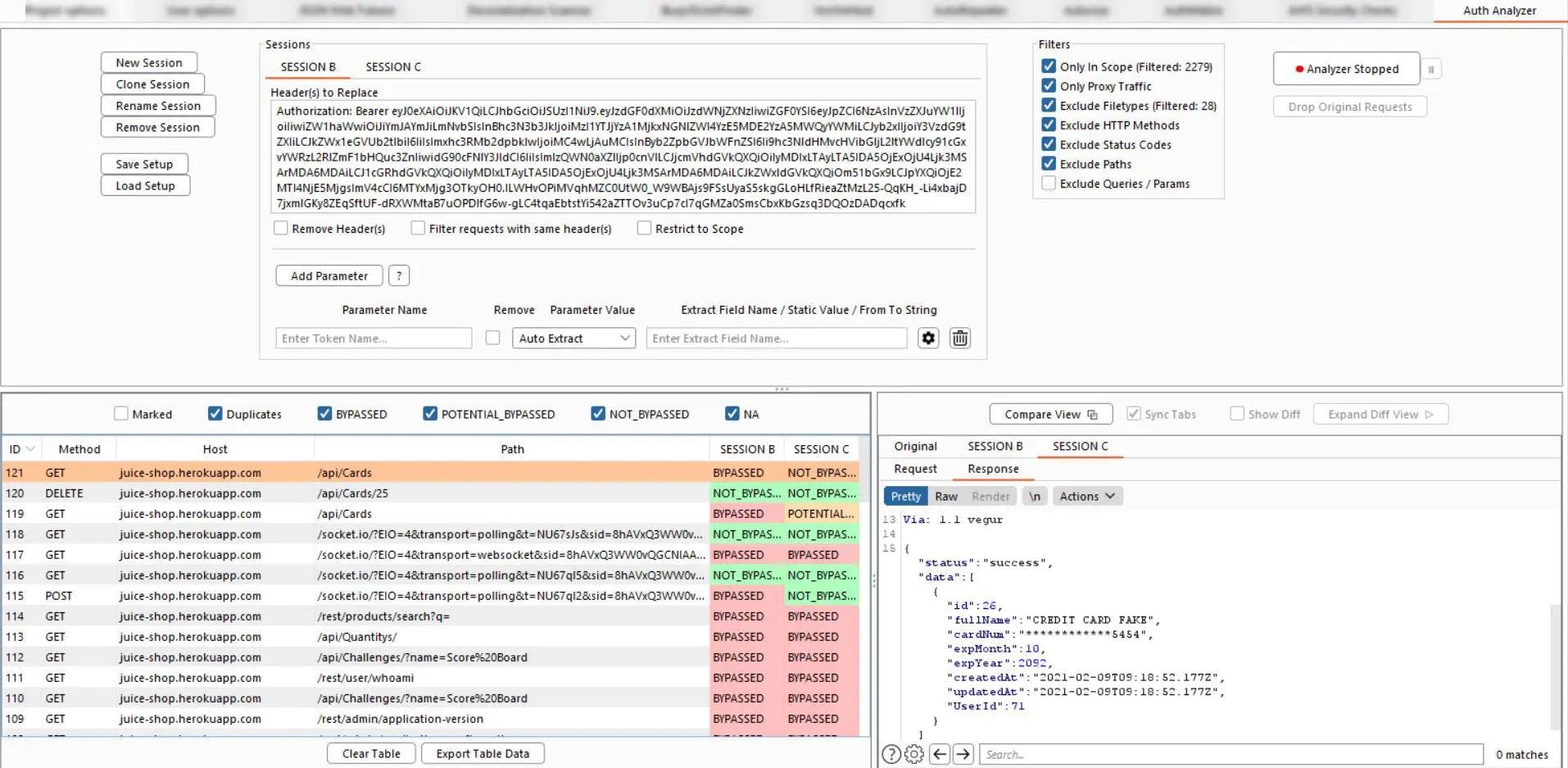
The plugin interface is really crowded and you can quickly get lost in the different options. Let’s get to the point:
- Sessions panel: this section is dedicated to your different users’ sessions and which header you want to replace.
- The “Add Parameter” button can be used to automatically replace the parameters value which can be in your path requests, URLs, headers, cookies…
- At the bottom half, you’ll find a “Request Viewer panel” to see which requests have been tested and which one could be bypassed.
When you select a particular request you can examine the request and the response on the lower right quadrant.
How to use it?
First, go on Extender > BApp Store and install Auth Analyzer extension. After a successful installation, you should see it appear in a new tab.
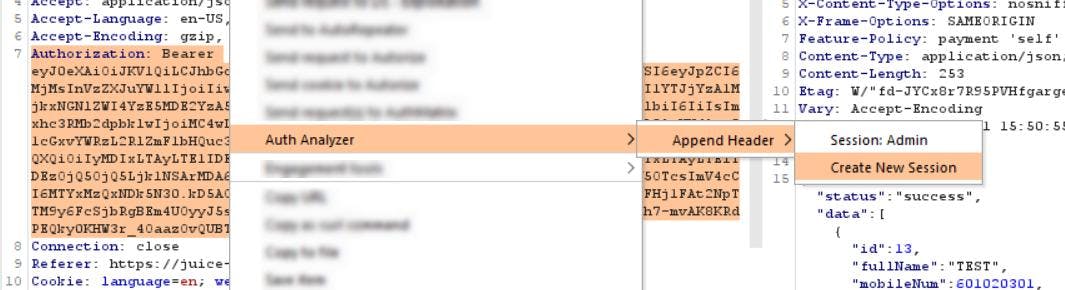
Start by creating two or more users’ profiles as needed in Auth Analyzer by clicking on the button New Session then copy/paste cookies and headers for auth. Alternatively, for each session, you can also go on your HTTP Proxy tab, right click on your session headers (cookie, authorization…) > Append Header > Create New Session.
Once you have created your different sessions with appropriate headers, you can come back to your target (with admin role for example) and navigate on it to generate some requests.
The plugin will automatically replay your queries with your different profiles.
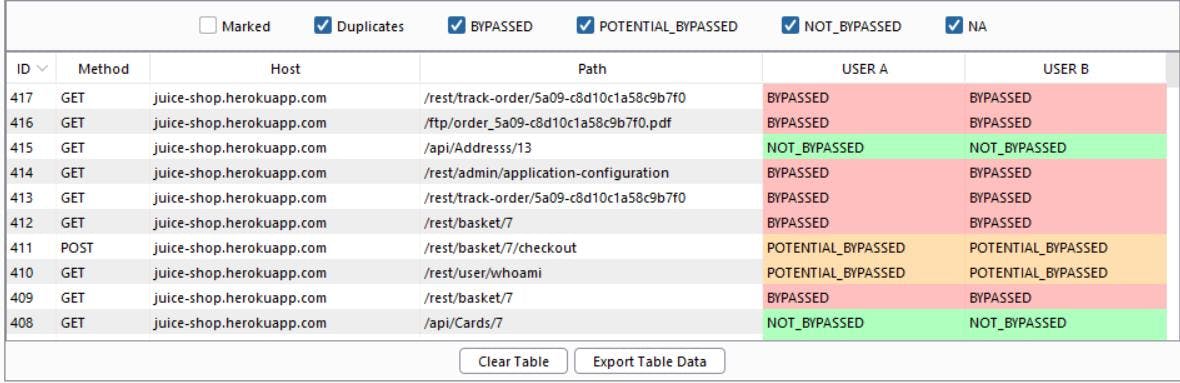
Each request will be highlighted with a specific color and status (bypassed, potential bypassed, no bypassed) to quickly identify if a bypass has been observed.
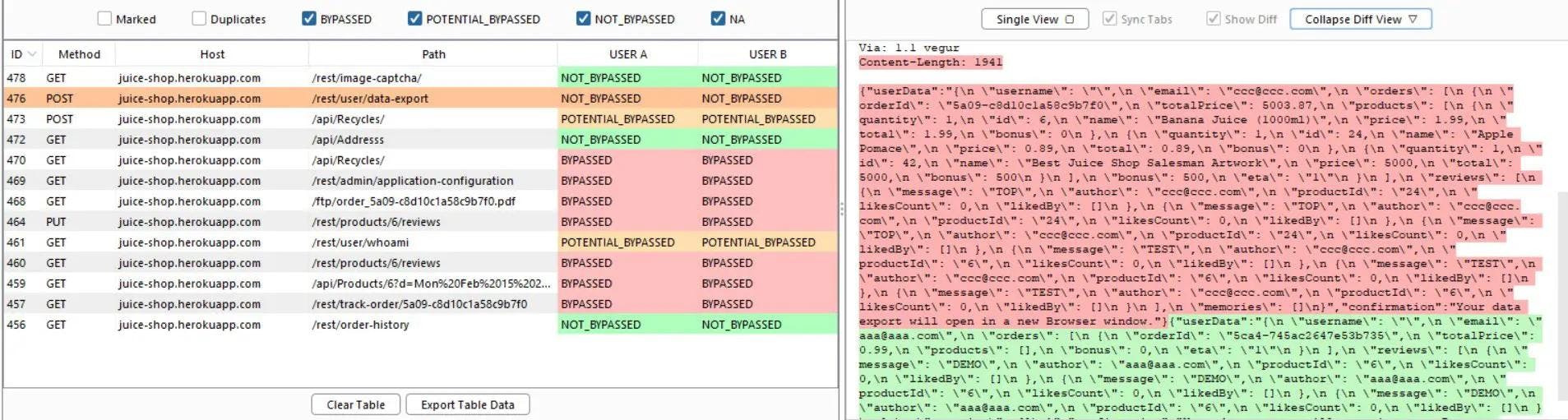
If one of your requests is identified to have an interesting behavior, you can quickly perform a “diff” to compare your sessions, and see which particular portion of your requests data are different (in request and in response) and possibly identify a specific parameter or endpoint which could be vulnerable.
You can see the requests (Original + your own sessions) in a divided window or in a “single view”. But, you can also use the “Expand Diff View” feature which is like the “Comparer” feature of Burp Suite but accessible directly in the same tab. The highlight will help you to quickly get every modification.
With this plugin, you have the possibility to define which parameters are being replaced or extracted before the request for the given session is repeated. It’s like the “match and replace” feature in a proxy on steroids. Several modes are available:
- Auto Extract: the parameter value will be extracted if it occurs in a response which contains the defined field name (works in Set-Cookie Header, HTML Document Response, JSON Response),
- Static Value: if you want to define a static parameter value,
- From String To String : useful when you want to replay a login process to auto extract and renew your sign-in, no need to copy/paste again your auth headers,
- Prompt for Input: auth analyzer will ask you to enter the value (for example in the scenario of an 2FA authentication).
For example, if your target uses a CSRF protection sheme, you can use the feature to auto extract the value of the CSRF token (works also for JavaScript files) and replace it with the right value.
By using Auth Analyzer, the author suggests to test for CORS misconfiguration, by auto replacing the value of Origin header and set an “HTTP Method” filter for all methods excluding the OPTIONS method.
Now you have a good global view of how to use Auth Analyzer, how this plugin can help you to find vulnerabilities like “privileges escalation” and how to test horizontal and vertical rights. Moreover, the GitHub repository with all the details is available here.
Have a good hunt and see you next time for a PimpMyBurp#3