Ethical hackers can make significant contributions to increasing products’ digital security. Still, the situation where a vulnerability is identified by an individual outside the organisation remains uneasy to handle for many organisations. To adequately address the discovery and interaction in such cases, a framework for coordinated vulnerability disclosure is needed.
In this instalment of our Vulnerability Coordination series, we take a closer look at the obstacles to coordinated disclosure and discuss a relevant framework for establishing a working process. Oh, and we have a neat infographic to sum all that food for thought—it is in English and en français, for you to peruse when raising awareness.
Obstacles to efficient vulnerability disclosure
Three significant barriers to a hacker’s participation in a coordinated vulnerability disclosure (CVD) process exist:
- Legal barriers or legal uncertainty;
- Lack of awareness about the appropriate existing means for disclosing a vulnerability;
- Insufficient or excessively slow communication with the system manager or coordinator.
It is thus essential to creating a legal and organisational environment in which the security researcher feels sufficiently protected and confident enough to report a vulnerability to the manager of the information system concerned, who will then ensure rapid remediation.
One way of solving those challenges is to pass appropriate legislation. To date, only individual EU Member States are considering the creation of such guidance at the national level. A weighty barrier to the implementation of schemes about countervailing duty policies in the EU is the absence of a single interpretation among the Member States of what constitutes “hacking”.
As a result, providing the legal security, necessary to ethical hackers involved in the discovery of vulnerabilities, is slow to materialise. Thankfully, the legislative approach is not the only one facilitating effective CVD. It is, so, essential to put appropriate disclosure processes in place through supplementary advice and better practices.
A framework for disclosure at the core of security governance
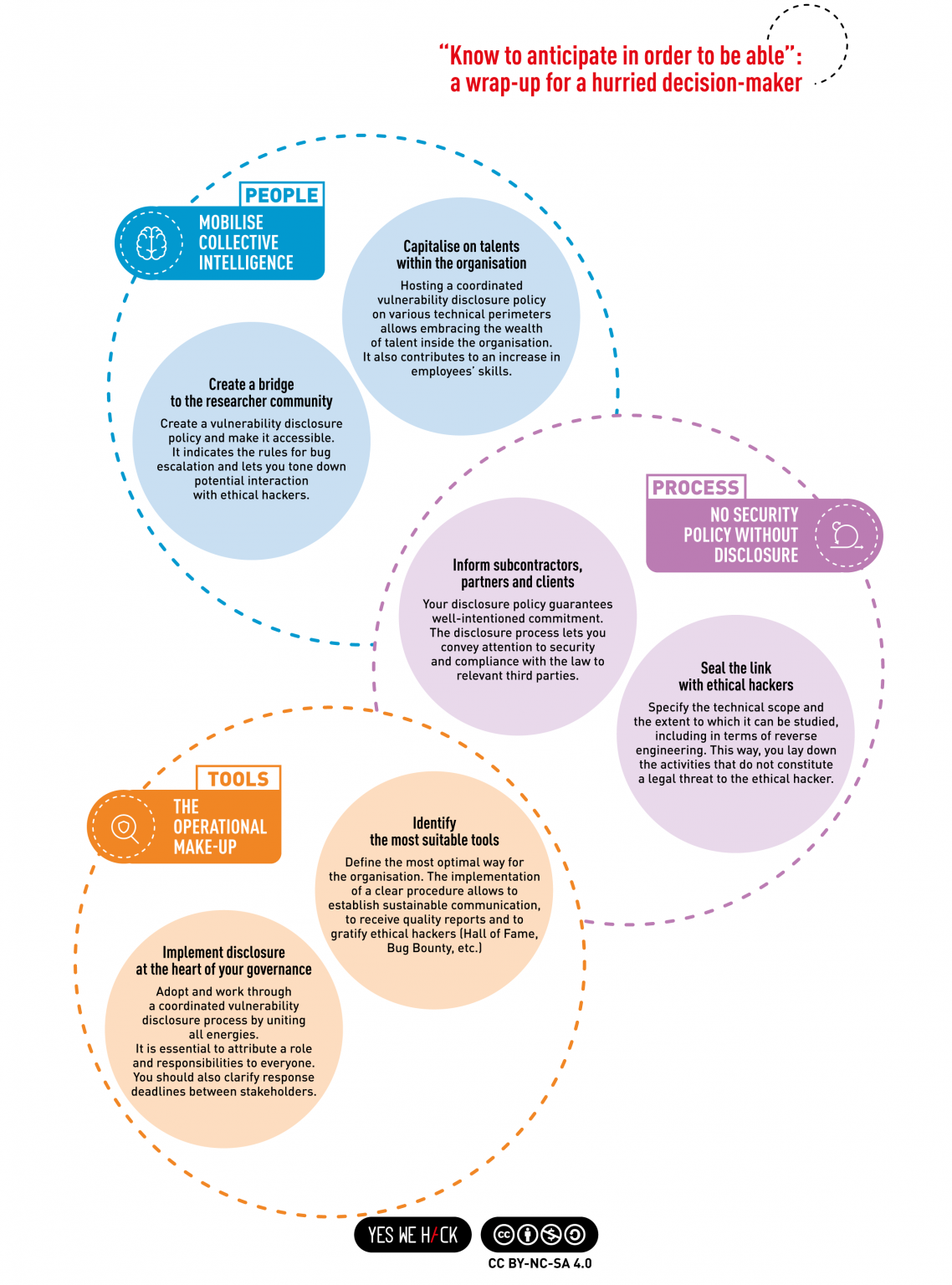
Coordinated vulnerability disclosure is a process, not an isolated event. Firstly, it requires stakeholders to understand their respective roles and responsibilities around vulnerability disclosure. Secondly, adopting the right tools enables people to act according to their responsibilities. Thirdly, connecting people to tools happens through processes and actions of (security) governance. Together, these three components create a healthy environment, encouraging collaboration and reducing digital risk over the long-term.
The people-process-tools triptych outlined just now is a robust non-legislative alternative to implementing CVD policies. Doing so involves a holistic approach that takes into account:
- The need to train all those involved, that is the teams in charge of managing the vulnerability escalations (reception, sorting, qualification, cascade towards the managers of assets in need of remediation, etc.);
- The presence of clear, known and up-to-date procedures for vulnerability disclosure: contact information, response deadlines, etc. The existence of a vulnerability disclosure policy should be publicised appropriately and visibly and in unambiguous terms;
- The proper tools for fitting procedures and actions into place, such as a secure communication channel (public or private bug bounty program, security.txt page, etc.).
The private sector has a leadership role to play in promoting appropriate frameworks, thus consolidating actual information sharing.
Summing up: Create a working framework for coordinated vulnerability disclosure
The global and lasting reduction of risk will come from the cooperation of both public and private actors. An international model in this field is essential to avoid all uncoordinated public disclosure. As such, guaranteeing protection for ethical security researchers is paramount.
We have created the infographic below to summarise the take-home messages on how to create a working framework for vulnerability disclosure. Below, you can download the high-resolution file in English and en français. It is free to use under the terms of the CC-by-NC-SA licence.