Cybersecurity is a more pressing priority than ever for US-listed companies and foreign private issuers in the wake of new rules and a landmark enforcement action from the US Securities and Exchange Commission (SEC).
The new SEC cyber rules, in force since 15 December, introduced mandatory reporting of “material” cybersecurity incidents and new annual disclosure obligations around cybersecurity risk management, strategy and governance.
A month earlier the SEC stunned the cybersecurity industry when it charged SolarWinds and its Chief Information Security Officer (CISO) with fraud and internal control failures related to a catastrophic cyber-attack in 2020 – an unprecedented move for the agency.
Even cybercriminals have noticed the SEC’s increasingly muscular approach to cybersecurity. In November, the BlackCat ransomware gang supposedly reported MeridianLink to the agency for failing to disclose BlackCat’s breach of the digital lending platform.
Added to increasingly numerous and sophisticated cyber-attacks, the SEC’s latest manoeuvres are certainly focusing minds in the boardroom (and not necessarily just for public companies).
With digital transformation ongoing and code vulnerabilities a leading attack vector, this article explains how a unified, multi-layered offensive security strategy is invaluable in reassuring both regulators and stakeholders about your security posture. To this end, for instance, YesWeHack’s all-in-one vulnerability management platform consolidates auto-scanning, Bug Bounty, pentest management, a vulnerability disclosure mechanism and attack surface management.
What are the new SEC cyber rules?
Public companies must now disclose in their annual filings “any cybersecurity incident they determine to be material” within four days of deeming it material, announced the SEC when the new SEC cybersecurity rules were adopted in July 2023. Their disclosure must “describe the material aspects of the incident’s nature, scope, and timing, as well as its material impact or reasonably likely material impact on the registrant.”
The SEC cybersecurity rules 2023 also require a description of “their processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats, as well as the material effects or reasonably likely material effects of risks from cybersecurity threats and previous cybersecurity incidents.”
Third and final, filings must “describe the board of directors’ oversight of risks from cybersecurity threats and management’s role and expertise in assessing and managing material risks from cybersecurity threats.”
These cybersecurity risk management and incident disclosure obligations require comparable disclosures by foreign private issuers.
The SEC cybersecurity rules’ effective date was 15 December 2023. ‘Smaller reporting companies’ have an additional 180 days before they must start disclosing ‘material’ incidents.
Why was the SolarWinds CISO charged by the SEC?
In November 2023, the SEC announced charges against SolarWinds, the observability and IT management platform, and its CISO, Timothy Brown, “for fraud and internal control failures relating to allegedly known cybersecurity risks and vulnerabilities”.
It was the first time the SEC had ever brought cybersecurity-related charges against a CISO.
The bombshell news relates to the nearly two-year-long ‘Sunburst’ attack, which compromised 18,000 SolarWinds customers via a backdoor implanted in a software update for IT performance monitoring system Orion. Microsoft, NASA and the US justice and state departments were among the victims.
The charges allege that “SolarWinds and Brown defrauded investors by overstating SolarWinds’ cybersecurity practices and understating or failing to disclose known risks”. Brown is also alleged to have “failed to resolve” certain “risks and vulnerabilities” or “at times, sufficiently raise them further within the company”.
The SEC cyber disclosure rules show the agency is getting serious about cybersecurity. Why?
The SEC, which enforces securities laws, appears to increasingly see cybersecurity as central to its mission of protecting investors and facilitating capital formation.
“Whether a company loses a factory in a fire – or millions of files in a cybersecurity incident – it may be material to investors,” explained SEC chair Gary Gensler upon the rules’ adoption. He said companies and investors would benefit if their cybersecurity disclosures “were made in a more consistent, comparable, and decision-useful way”.
On the eve of the new rules coming into effect, Erik Gerding, director of the SEC’s corporation finance division, said the trajectory of multiple trends highlighted “investors’ need for improved disclosure” about cybersecurity issues. Namely, he cited the AI threat and increases in the digitisation of economic activity, remote work, the profitability of cyber-attacks, the use of digital payments, and reliance on third-party cloud and IT service providers.
Gerding also noted the rising costs – up to $4.45 million per data breach in 2023, according to IBM – associated with successful cyber-attacks.
Far from simply encouraging “boilerplate disclosures”, Gerding said the new cybersecurity disclosure requirements should elicit “tailored disclosures” that help investors evaluate even “emergent or evolving” risks.
Do the SEC cybersecurity rules for public companies affect other organisations?
The new SEC rules on cybersecurity apply directly only to US-listed companies and foreign private issuers.
Organisations not subject to SEC oversight might nevertheless see its new rules as offering a useful framework for being transparent with their own stakeholders.
Moreover, with software supply chain attacks increasing, privately-held organisations can still be held liable as third-party suppliers implicated in cybersecurity incidents disclosed by public companies.
The SEC has not shied away from launching enforcement actions against private entities, most famously over the Theranos blood-testing scandal that landed founder Elizabeth Holmes in prison. More recently, the SEC has targeted private clean energy company Monolith Resources and, in relation to the Microsoft Hafnium cyber-attack, a private law firm, Covington & Burling.
The new SEC cybersecurity rules and SolarWinds charges are also part of a wider regulatory trend – propelled by the White House’s cybersecurity-focused executive order of 2021 – making stringent cybersecurity controls a greater legal and compliance imperative.
The trend is global. Across the Atlantic, for instance, the EU Cybersecurity Act, Cyber Resilience Act and – as covered by a recent YesWeHack article – Digital Operational Resilience Act (DORA) are imposing new compliance requirements on organisations operating within the EU.
What are the implications of the SEC cybersecurity disclosure rules for my cyber-risk management strategy?
In mandating greater transparency and consistency in registrants’ cybersecurity disclosures, the SEC will hope to encourage a more rigorous approach to cyber-risk management.
Specifically how those risks are mitigated amid fast-evolving threats and technology is left to organisations to judge.
“In order to address a potential misconception, the Commission is not seeking to prescribe particular cybersecurity defenses, practices, technologies, risk management, governance, or strategy,” said Erik Gerding. “Public companies have the flexibility to decide how to address cybersecurity risks and threats based on their own particular facts and circumstances.”
In unifying and streamlining offensive security testing and its outcomes, the YesWeHack platform suits organisations of various sizes, sectors and levels of security maturity. It also offers increasingly powerful security benefits in the context of the current threat and infosec industry landscape.
How can I proactively improve my cyber-risk management strategy with YesWeHack in light of the SEC cybersecurity rules?
Our platform can help public companies enhance their SEC disclosures around “assessing, identifying, and managing material risks from cybersecurity threats”.
How? First, our Vulnerability Disclosure Policy (VDP) product provides a simple, standardised mechanism for receiving external vulnerability reports.
A VDP is useful preparation for a Bug Bounty Program, which is inherently more scalable, draws on a much broader skills base and has fewer methodological constraints than traditional security testing. As such, this form of crowdsourced security testing reliably surfaces serious vulnerabilities even on heavily-pentested scopes.
A Bug Bounty Program extends and maximises your security testing coverage through an unlimited pool of ethical hackers and a continuous, flexible audit of your growing attack surface.
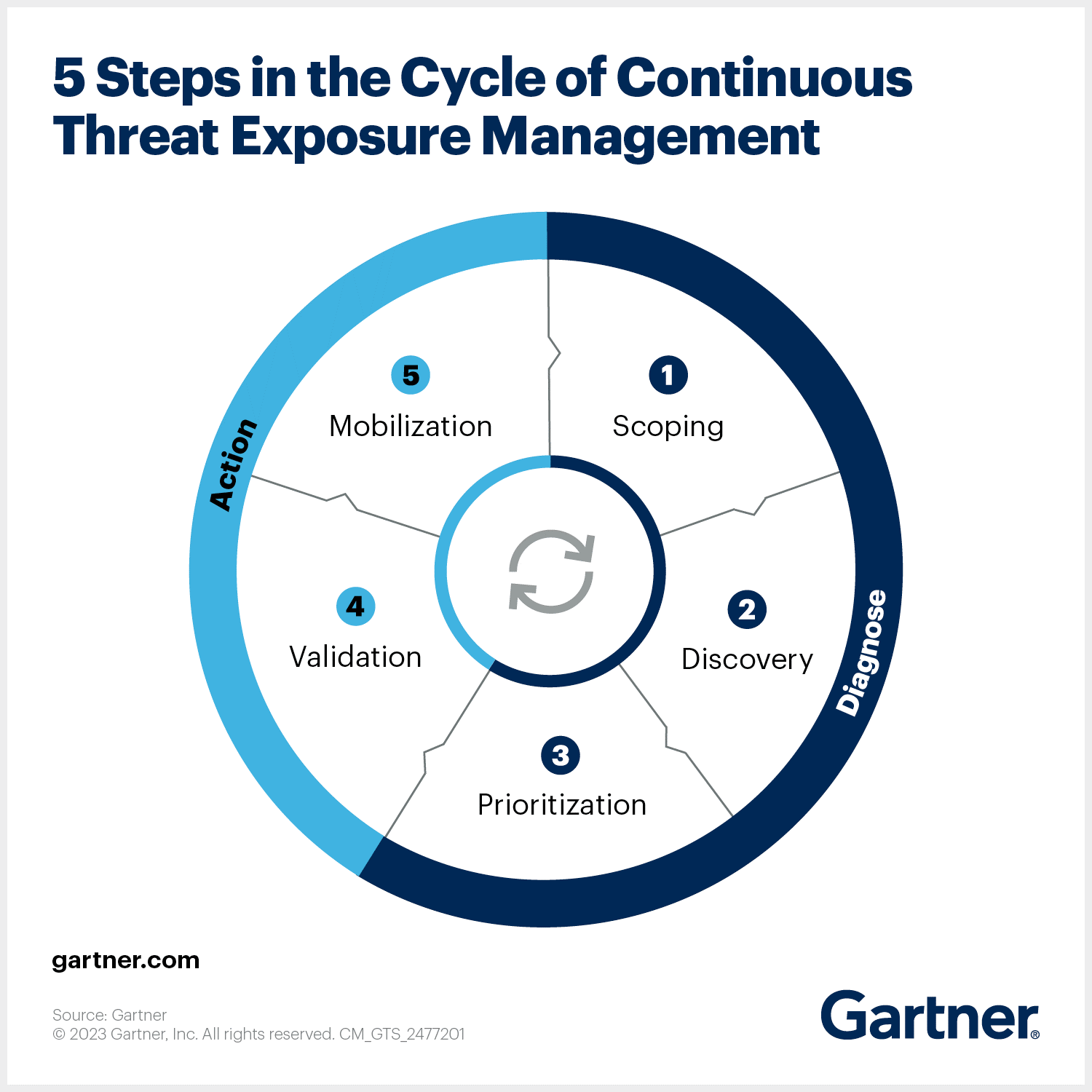
But to comprehensively secure your attack surface, you must first understand its size and composition. Hence Gartner cited continuous Attack Surface Management (ASM) as a top strategic technology trend for 2024.
We recently launched an ASM product that gives a real-time, comprehensive picture of your attack surface (including the third-party assets that the SEC’s Erik Gerding expressed concern about).
The ASM, which leverages a Continuous Threat Exposure Management (CTEM) model, also detects your online assets’ exposure to known vulnerabilities and provides automated, risk-based prioritisation of those security flaws.
How can I reassure investors or other stakeholders over our cybersecurity posture given budgetary and recruitment challenges?
More than one-third of CISOs reported flat or shrinking cybersecurity budgets in 2023, while the global shortfall in infosec skills reached a record four million in 2023.
Fortunately, the YesWeHack platform can both increase the cost-effectiveness of your OffSec strategy and unlock access to various skills – from problem solving to cloud security – apparently lacking in the current infosec jobs market.
YesWeHack offers a pay-by-results testing model (paying only for valid, actionable bugs, according to severity), and substantially streamlines vulnerability management and remediation.
For instance, our Pentest Management solution consolidates pentest findings from all providers into one, user-friendly reporting interface. Similarly, the overall YesWeHack platform combines asset discovery with vulnerabilities from various sources – ASM auto-scanning, pentests, Bug Bounty, VDP – into a single interface.
The result is a unified, comprehensive and risk-based approach to security testing.
What do the SEC’s new cybersecurity rules and enforcement stance mean for the role of CISOs and senior executives?
In addressing boardroom-level oversight of cybersecurity risk management, the new SEC cyber rules are a firm reminder to CISOs and other senior executives that they bear ultimate responsibility for their organisation’s cybersecurity posture. The SolarWinds action serves notice that they can be held to account if they fall short.
“It’s clear that delegating oversight entirely to the security team, striving merely for ‘box-ticking’ compliance, or simply throwing money at the cybersecurity problem will no longer suffice,” says Rodolphe Harand, managing director of YesWeHack. “More than ever, CISOs must frequently ‘reality check’ their online risks.
“To this end, they must source the best, most cost-effective processes and technologies for the proactive discovery, evaluation and mitigation of risks – and in a way that is easy to convey to regulators and their stakeholders. We believe the YesWeHack platform can efficiently facilitate these goals.”
The YesWeHack platform provides real-time visibility of your potential attack vectors and a unified, multi-layered model for uncovering, prioritising and remediating vulnerabilities. It also provides functionality that facilitates the production of what the SEC calls “consistent, comparable, and decision-useful” disclosures.
This includes:
- Real-time tracking of vulnerability reports
- Interactive dashboards and metrics
- Real-time view of your ‘asset coverage’ – ie, seeing which assets are currently being tested, by which methods, and the outcomes so far
- Integrations with popular bug-tracking tools
- Ability to certify compliance and share vulnerability information with authorities via dashboards and one-click generation of proofs of audit and exportable executive summaries
YesWeHack’s GDPR compliance, CREST accreditation plus ISO 27001 and ISO 27017 certifications can give stakeholders further reassurance. The same applies to our zero-trust network, bombproof infrastructure and state-of-the-art encryption, among other trust and security guarantees.
Proactive, multilayered and unified security testing is a strategic investment. CONTACT OUR SALES TEAM to BOOK A DEMO of our Bug Bounty service or ASM, and to find out more about how your organisation can secure your growing attack surface cost-effectively.