Adapt tests to your IT needs, whether you run CI/CD or more traditional project lifecycles. Seamlessly integrate vulnerability reports with your tools and workflows. Reduce time to detection and remediation.
UNLEASH THE POWER
OF OUR HUNTERS
WITH BUG BOUNTY
The most cost-effective layer in your security stack
EXTEND YOUR TESTING CAPABILITIES AND MAXIMISE TEST COVERAGE WITH BUG BOUNTY PROGRAMS
A Bug Bounty program gives you access to a diverse, unlimited pool of skilled security researchers.
Our community of hunters provides a continuous audit of your growing attack surface to uncover high impact vulnerabilities – even on heavily-pentested scopes.
Connect your security, IT and dev teams with our security researchers. Enable knowledge sharing, raise security awareness and instil security ownership to reduce the creation of vulnerabilities early in project lifecycles.
Pay only for valid, actionable reports, according to your priorities – reducing the “price per vulnerability”. Extract maximum value from your testing budget by continuously fine-tuning your program.
WHY CHOOSE YESWEHACK?
FULLY MANAGED SERVICE TAILORED TO YOUR NEEDS
Our Customer Success Management team supports you along every step of your Bug Bounty journey – from designing the program to fine-tuning and scaling it up, at your own pace.
Understanding that "one size does not fit all", we provide support to suit your security, IT and budget requirements.
We can help you choose between a private or public program; set your budget; craft your rules and rewards grid; select, rotate and communicate with researchers; and continuously optimise rewards, scopes and qualifying vulnerabilities.
IN-HOUSE TRIAGE SERVICE
Don’t waste time reviewing incoming reports – our renowned team of expert, in-house triagers can perform the task for you as part of our fully managed service.
YesWeHack does not outsource this critical function to bug hunters or other third parties, to ensure triage quality, consistency and confidentiality.
Our triage team eliminates duplicate reports, validates each bug, reproduces Proofs of Concept, sets severity and advises your team on interactions with hunters – effectively acting as an extension of your SecOps function.
PROTECTING ANY ORGANISATION FROM SMALL BUSINESSES TO enterprises
Find out more about our product features
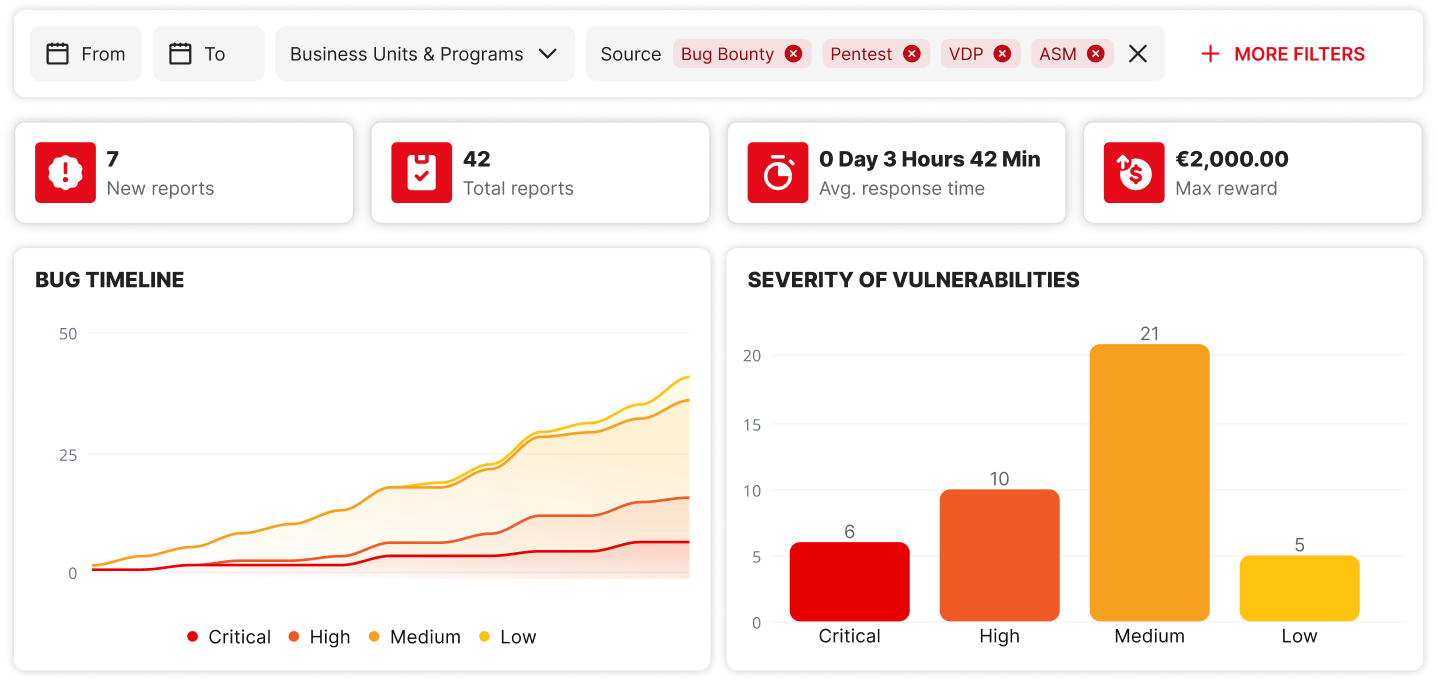
ADVANCED DASHBOARDING AND COMPLIANCE FEATURES
- Track the performance of your program through interactive dashboards that display real-time metrics.
- Generate a proof of audit and fulfil compliance requirements with an exportable Executive Summary.
CHOOSE YOUR BUG BOUNTY PROGRAM
PRIVATE BUG BOUNTY PROGRAM
Private Bug Bounty programs are restricted to a specific number of handpicked security researchers and the program rules are not publicly disclosed.
YesWeHack chooses hunters whose skillset and experience are best suited to your assets, budget and testing requirements. Only thoroughly vetted and high-ranking hunters are eligible for private programs.
PUBLIC BUG BOUNTY PROGRAM
Public Bug Bounty programs are open to our entire community of ethical hackers and their basic details are publicly disclosed.
By crowdsourcing security testing at such scale, you can potentially maximise test coverage and showcase your commitment to security to your customers, partners, and shareholders.
LIVE HACKING EVENT
A Live Hacking Event is a time-bound Bug Bounty competition that hunters typically attend in person, although they can be conducted virtually too.
This Live Bug Bounty gives your IT and security teams an invaluable opportunity to meet and learn from the world’s finest security researchers, who can enhance their own performance by collaborating with their peers.
YesWeHack will help you assess the feasibility of such an event, support you in its planning and budgeting, and select the hunters with the most suitable skillsets.
WHAT OUR CUSTOMERS HAVE TO SAY
“We have discovered vulnerabilities that were beyond our imagination. Considering the cost, running a Bug Bounty program proves to be immensely beneficial for a company.”
“As we deliver continuously, the ability to extend the scope of our program at the click of a button makes us much more agile. As soon as an application is updated, we can have it tested, fix bugs and easily set up a feedback loop.”
“Thanks to our Bug Bounty Program, awareness has been raised internally. We all know now that security is not a luxury but a necessity.”
We have discovered vulnerabilities that were beyond our imagination. Considering the cost, running a Bug Bounty program proves to be immensely beneficial for a company.